Revolutionize Your Network Security with
Agentless Zero Trust Application Access from Perimeter81
28
Years of Experience
700+
Satisfied Customers Globally
95%
Client Retention Rate
1200+
Cyber Security Projects
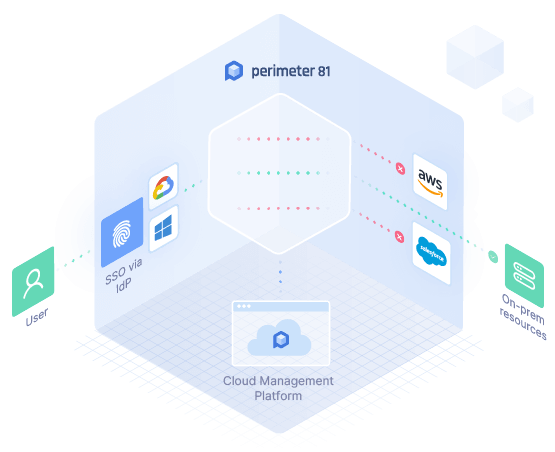
Zero Trust VPN Access
In today’s digital landscape, traditional network security measures are no longer sufficient to combat the sophisticated threats facing businesses. Enter Agentless Zero Trust Application Access, a groundbreaking solution that redefines network security paradigms and empowers organizations to safeguard their critical assets with unparalleled efficacy.
At AiCyberWatch, we are proud to offer this cutting-edge technology as part of our comprehensive suite of cybersecurity solutions tailored to the unique needs of businesses in Asia.
What is Agentless Zero Trust Application Access?
Agentless Zero Trust Application Access represents a paradigm shift in network security, moving away from the traditional perimeter-based approach to a more dynamic and proactive model. Unlike conventional security methods that rely on static perimeters and trust-based authentication, Agentless Zero Trust Application Access adopts a “never trust, always verify” philosophy.
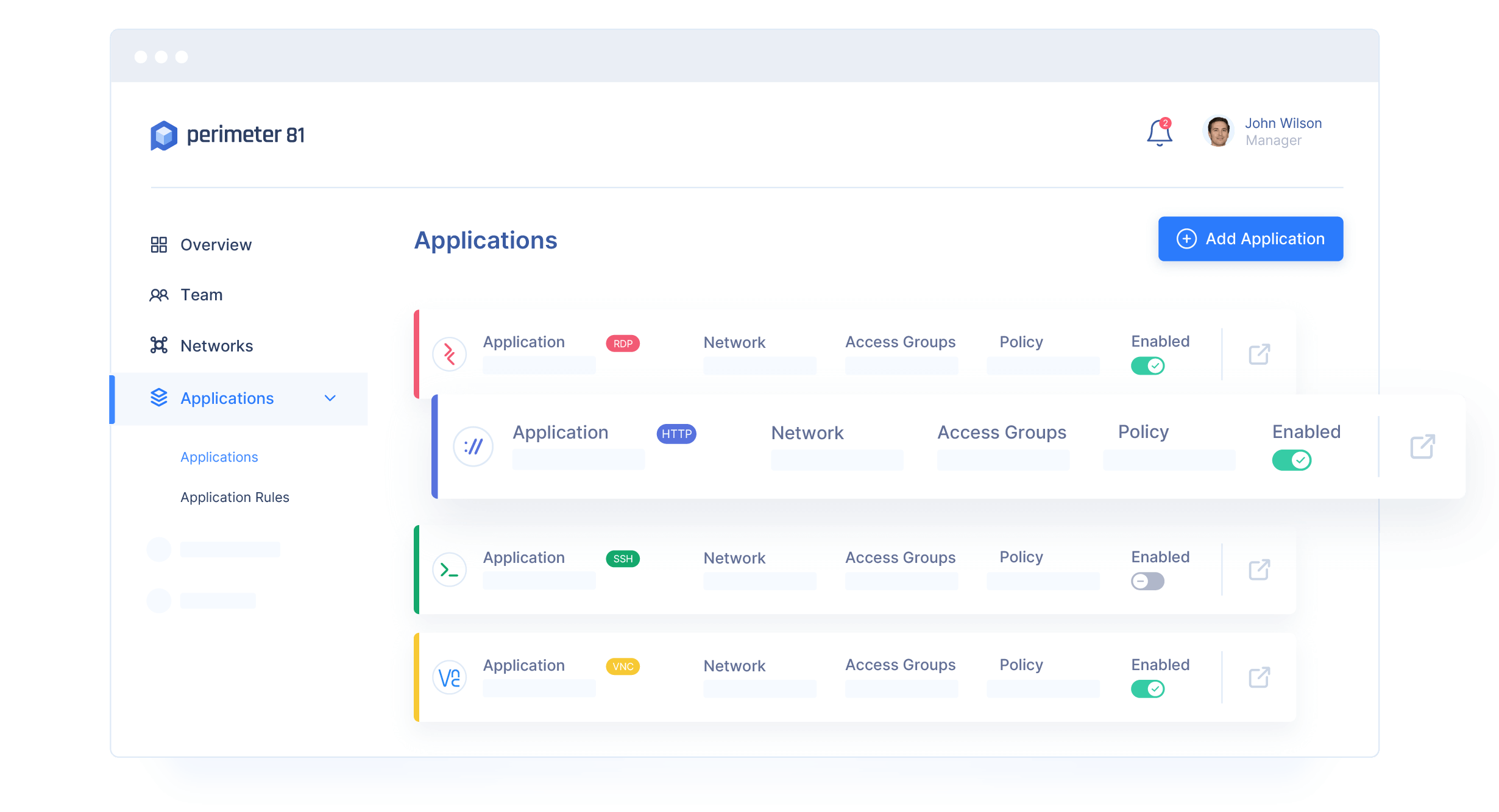
Key Features and Benefits:
Secure Anywhere, Anytime Access
With Agentless Zero Trust Application Access, users can securely access applications and resources from any location, at any time, without the need for a VPN or traditional network perimeter. This ensures seamless connectivity and productivity for remote and mobile workforce.
Granular Access Control
This solution provides granular control over user access permissions, allowing organizations to define and enforce access policies based on various factors such as user identity, device posture, location, and behavior. By implementing least-privilege access principles, organizations can minimize the risk of unauthorized access and data breaches.
Application-Centric Security
Unlike network-centric security approaches, Agentless Zero Trust Application Access focuses on securing individual applications and resources rather than the entire network. By implementing micro-segmentation and application-level encryption, organizations can mitigate the risk of lateral movement and limit the blast radius of potential security incidents.
Simplified Deployment and Management
With its agentless architecture, this solution offers simplified deployment and management, reducing the overhead associated with traditional VPN solutions. Centralized management consoles provide administrators with real-time visibility into user activity and security posture, enabling rapid threat detection and response.
Enhanced User Experience
By eliminating the need for cumbersome VPN clients and complex authentication processes, Agentless Zero Trust Application Access delivers a seamless and frictionless user experience. This improves user productivity and satisfaction while maintaining robust security controls.
Why Choose Aicyberwatch for Agentless Zero Trust Application Access?
At AiCyberWatch, we understand the evolving threat landscape facing businesses today, and we are committed to providing innovative cybersecurity solutions that empower organizations to stay ahead of emerging threats. Our team of experts will work closely with you to design, implement, and manage a customized Agentless Zero Trust Application Access solution tailored to your specific requirements, leveraging our partnership with Perimeter81
With our extensive experience and proven track record in the cybersecurity industry, you can trust Aicyberwatch to deliver reliable, scalable, and cost-effective security solutions that meet the highest standards of excellence.
Take the first step towards enhancing your organization’s security posture and embracing the future of network security with Agentless Zero Trust Application Access from Aicyberwatch. Contact us today to learn more about our comprehensive cybersecurity solutions and how we can help protect your business from evolving threats.

Secure your apps now:
Our Clients
They Trust Us…So Can You!
Get In Touch With Us
Test the effectiveness of your own security controls before malicious parties do it for you.
Our security experts are here to help — schedule a call today.









 Call Us
Call Us