Data Loss Prevention as a Service
It refers to the process of identifying and assessing vulnerabilities in a system or network and then testing those vulnerabilities to determine whether they can be exploited to gain unauthorized access or perform other malicious activities.
Get a FREE Security Consultation
DLP as a Service
What is Data Loss Prevention (DLP)?
A DLP solution protects your data against unauthorised use and prevents unauthorised sharing or transfer of sensitive data. Data Loss Prevention solution comprises of a set of tools and processes that help detect and prevent unauthorized access, unwanted destruction, and exfiltration of sensitive data.
- Conduct Risk Assesment
- Identify key problems
- Help choose ideal DLP Solution
- Prepare Impementation paln & deploy
- Train the teams
- Ongoing monitoring & fine tuning

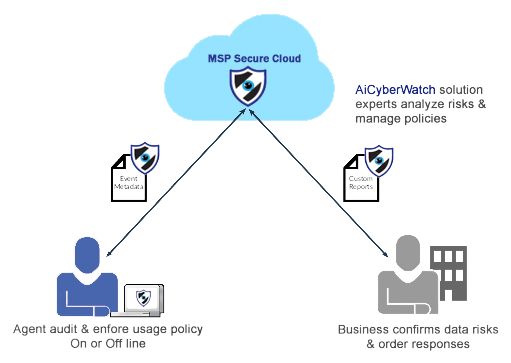
How does DLP as a Service work?
DLP as a Service is same as an on-premise solution minus the worries of people and technical expertise with absolutely same levels of protection & monitoring. A Managed DLP service can cater to organizations of any size across industries, mainly due to the ease of integration and deployment. DLP as a service supports quick deployment and scalability thus making it ideally suited for startups and other growing organisations.
Key features of DLP Solution Discover, Monitor, and Protect Your Sensitive Data
Device Control
Content-Aware Protection
eDiscovery
Enforced Encryption
Why should you trust us to Protect your Company’s sensitive data?
- Use of industry-leading DLP solutions tailored for protecting your sensitive data like personally identifiable information(PII) and intellectual property(IP).
- Enable remote deployment to ensure security and compliance for employees working in hybrid/remote environments
- Trained & Experienced solution architects and engineers managing operations
- 24/7 Monitoring of alerts and activity
- Ability to cover on-premise, fully cloud based and hybrid environments
- Full support to comply with regulatory requirements like HIPAA, PCI DSS etc.
Benefits of a Managed DLP as a Service
- Lower Complexity than traditional, on-premise solutions
- Higher speed of deployment and scalability
- Eliminate hassles of having in house technical teams
- Leverage and integrate learnings from wide pool of global customers
Showcase Of Our Recognized Clients
We Helped Hundreds of Businesses was Back on its Feet. Ut id urna tristique est tincidunt.

Global Manufacturing Industry

Health and Coaching platform

SAAS-based Software Solution provider
Trusted by Industry Leaders




Our Partners














Frequently Asked Questions
1. What is VAPT?
VAPT (Vulnerability Assessment and Penetration Testing) is a comprehensive process designed to identify and address security vulnerabilities in your IT infrastructure. It involves two key components: vulnerability assessment, which identifies potential weaknesses, and penetration testing, which actively exploits these weaknesses to understand their impact.
2. Why is VAPT important for my business?
3. How long does a VAPT engagement typically take?
A VAPT engagement typically takes between one to four weeks, depending on the scope and complexity of the assessment. This duration includes initial scoping, vulnerability assessment, penetration testing, and reporting. Larger or more complex environments may require additional time for thorough testing and analysis.
4. How does AiCyberWatch conduct a VAPT audit?
- Initial Scoping: Understanding your business and IT environment.
- Vulnerability Assessment: Scanning and identifying potential security vulnerabilities.
- Penetration Testing: Actively exploiting identified vulnerabilities to assess their impact.
- Reporting: Providing a detailed report with findings and recommended remediation steps.
- Remediation Support: Assisting in fixing the vulnerabilities to enhance your security posture.
5. How often should VAPT be conducted?
The frequency of VAPT depends on several factors, including the size and nature of your business, regulatory requirements, and the sensitivity of the data you handle. Generally, it is recommended to perform VAPT at least once a year or whenever significant changes are made to your IT infrastructure.
6. Why choose AiCyberWatch as your VAPT service provider?
AiCyberWatch stands out as a premier VAPT service provider in India due to our:
- Experienced Professionals: A team of certified and skilled cybersecurity experts.
- Advanced Tools and Techniques: Utilization of the latest tools and methodologies.
- Customized Solutions: Tailored VAPT services to meet your specific needs.
- Comprehensive Reporting: Detailed and actionable reports.
7. How can I get started with AiCyberWatch’s VAPT services?
Getting started with AiCyberWatch’s VAPT services is simple. Contact us or call our customer support. We will schedule an initial consultation to understand your requirements and provide a customized proposal.
8. What is the cost of VAPT services?
The cost of Vulnerability Assessment and Penetration Testing (VAPT) services can vary widely based on several factors, including the scope of the assessment, the size and complexity of the IT infrastructure, the type of testing required, and the specific needs of the organization.


